ME0 MbedTLS中间件
-
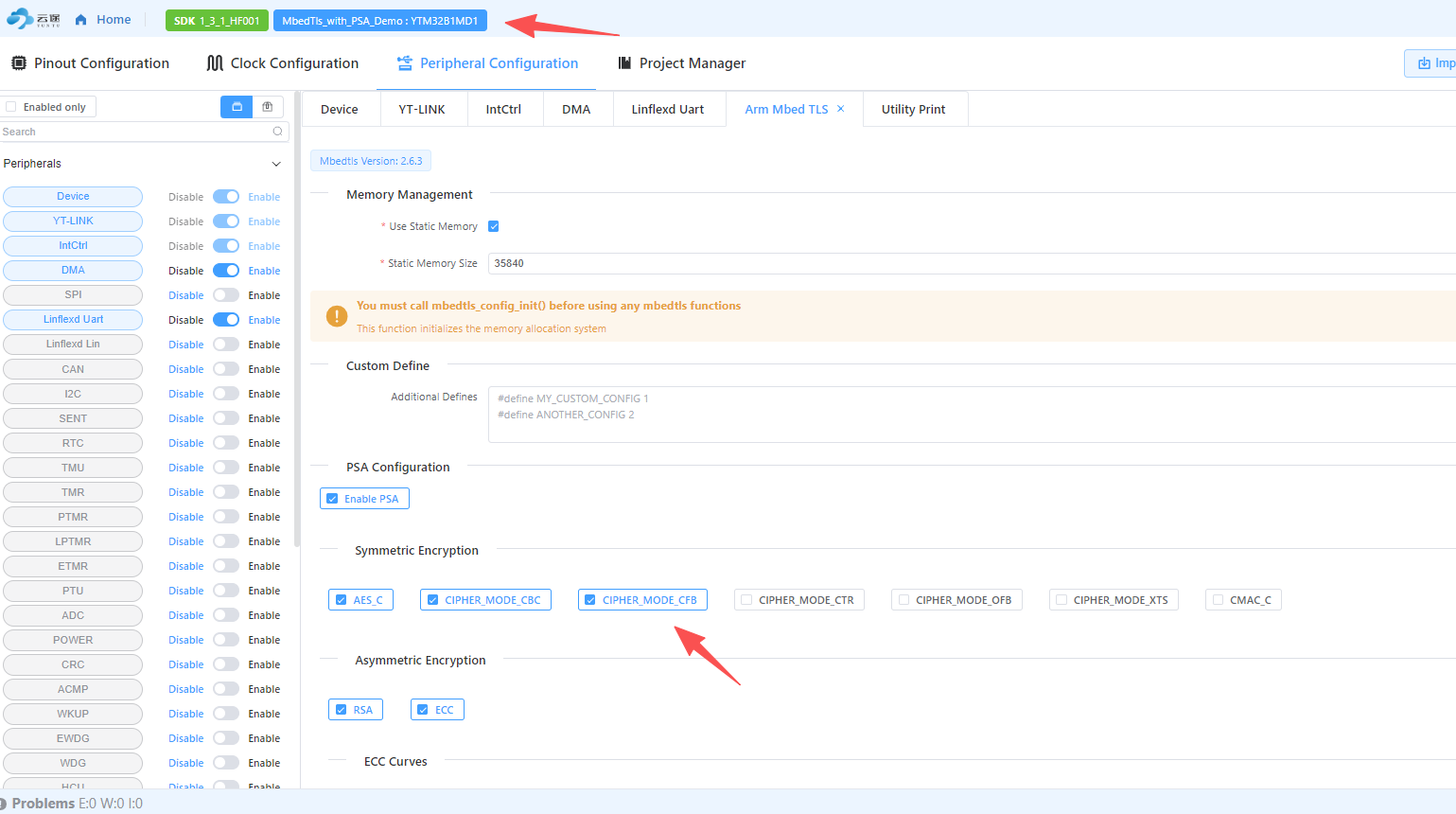
有个基于demo修改的增加函数
int aes_CFB_test(void) {
psa_status_t status;
psa_key_attributes_t attributes = PSA_KEY_ATTRIBUTES_INIT;
psa_key_id_t key_id = 0;
size_t output_length;
psa_cipher_operation_t operation = PSA_CIPHER_OPERATION_INIT;
uint8_t iv[16] = {
0x00, 0x01, 0x02, 0x03, 0x04, 0x05, 0x06, 0x07, 0x08,
0x09, 0x0a, 0x0b, 0x0c, 0x0d, 0x0e, 0x0f}; // Initialization vector for
// CFB mode/* Set key attributes for AES-CFB*/
psa_set_key_usage_flags(&attributes,
(PSA_KEY_USAGE_ENCRYPT | PSA_KEY_USAGE_DECRYPT));
psa_set_key_algorithm(&attributes, PSA_ALG_CFB);
psa_set_key_type(&attributes, PSA_KEY_TYPE_AES);
psa_set_key_bits(&attributes, 128);/* Import the key*/
status = psa_import_key(&attributes, aes_key, sizeof(aes_key), &key_id);
if (status != PSA_SUCCESS) {
PRINTF("Key import failed! (status = %d)\n\r", status);
return status;
}/* Performing encryption*/
CM33_DWT_Start(); // Start timing for encryption
status = psa_cipher_encrypt_setup(&operation, key_id, PSA_ALG_CFB);
if (status != PSA_SUCCESS) {
PRINTF("Encryption setup failed! (status = %d)\n\r", status);
psa_destroy_key(key_id);
return status;
}status = psa_cipher_set_iv(&operation, iv, sizeof(iv));
if (status != PSA_SUCCESS) {
PRINTF("Setting IV failed! (status = %d)\n\r", status);
psa_cipher_abort(&operation);
psa_destroy_key(key_id);
return status;
}status = psa_cipher_update(&operation, plaintext, sizeof(plaintext),
ciphertext, sizeof(ciphertext), &output_length);
if (status != PSA_SUCCESS) {
PRINTF("Encryption update failed! (status = %d)\n\r", status);
psa_cipher_abort(&operation);
psa_destroy_key(key_id);
return status;
}status =
psa_cipher_finish(&operation, ciphertext + output_length,
sizeof(ciphertext) - output_length, &output_length);
if (status != PSA_SUCCESS) {
PRINTF("Encryption finish failed! (status = %d)\n\r", status);
psa_cipher_abort(&operation);
psa_destroy_key(key_id);
return status;
}// Stop timing and calculate encryption time
uint32_t encryption_cycles = CM33_DWT_Stop();
PRINTF("AES CFB encryption took %u cycles\r\n", encryption_cycles);
PRINTF("CPU core clock frequency: %u Hz\r\n", cpu_freq);
PRINTF("AES CFB encryption time: %.6f seconds\r\n",
(float)encryption_cycles / cpu_freq);print_buf("Key", aes_key, DATA_LENGTH);
print_buf("IV", iv, DATA_LENGTH);
print_buf("Plaintext", plaintext, DATA_LENGTH);
print_buf("Ciphertext", ciphertext, DATA_LENGTH);/Performing decryption/
uint8_t decrypted[DATA_LENGTH];
status = psa_cipher_decrypt_setup(&operation, key_id, PSA_ALG_CFB);
if (status != PSA_SUCCESS) {
PRINTF("Decryption setup failed! (status = %d)\n\r", status);
psa_destroy_key(key_id);
return status;
}status = psa_cipher_set_iv(&operation, iv, sizeof(iv));
if (status != PSA_SUCCESS) {
PRINTF("Setting IV failed! (status = %d)\n\r", status);
psa_cipher_abort(&operation);
psa_destroy_key(key_id);
return status;
}status = psa_cipher_update(&operation, ciphertext, sizeof(ciphertext),
decrypted, sizeof(decrypted), &output_length);
if (status != PSA_SUCCESS) {
PRINTF("Decryption update failed! (status = %d)\n\r", status);
psa_cipher_abort(&operation);
psa_destroy_key(key_id);
return status;
}status = psa_cipher_finish(&operation, decrypted + output_length,
sizeof(decrypted) - output_length, &output_length);
if (status != PSA_SUCCESS) {
PRINTF("Decryption finish failed! (status = %d)\n\r", status);
psa_cipher_abort(&operation);
psa_destroy_key(key_id);
return status;
}print_buf("Decrypted", decrypted, DATA_LENGTH);
if (buf_cmp(plaintext, decrypted, DATA_LENGTH) != 0) {
PRINTF("Decryption failed! (status = %d)\n\r", status);
psa_destroy_key(key_id);
return -1;
}/* Destroy the key*/
psa_destroy_key(key_id);
return 0;
}可以参考一下。
快速上手云途开发生态
发帖前请查看
帮助改进和优化YT CONFIG TOOL,有机会抽取YTM32B1ME0 EVB哦...
